Why
Microsoft DNS Server has had its share of vulnerabilities. So why are we allowing a Tier0 system to access the internet at all? One of the most notorious examples is CVE-2020-1350—a critical remote code execution vulnerability in Windows DNS Server that could be triggered by a crafted DNS query, making it wormable and earning the highest severity rating.
The only zones that the domain controllers should reply for are:
- <domain fqdn>
- _msdcs.<domain fqdn>
Yes, there are cases where we have a forest etc.. but you still get the point.
sequenceDiagram
participant Clients
participant DomainControllers
participant ScaryInternet
Clients->>Clients: User is tricked into visiting a site
Clients->>DomainControllers: DNS query for badactor.example.com
DomainControllers->>ScaryInternet: Forward DNS query
ScaryInternet-->>DomainControllers: “Whatever they want”
DomainControllers-->>Clients: Return response from BadActor
Note over Clients, DomainControllers: If there’s a bug in the, we lose
Okey, but I have configured my Domain Controller to forward all queries to my DNS vendor. So I am safe. You are as safe as your DNS provider. But why risk them being wrong. It is better to just move away from using Tier0 things for everyday services.
Solutions
Build your own Linux
Build two machines. There are multiple DNS software available for Linux. Just make sure to forward the AD zones to the Domain Controllers This is a good time to AnyCast your DNSes.
Build your own in Windows
Just setup two Windows server. Add make sure to add conditional forwarders to the real domain controllers for the zones hosted there. This is a good time to AnyCast your DNSes.
Unifi Eco system
Unifi is a good solution for homes and small businesses. Unifi only allows to forward DNS to a single DNS server.
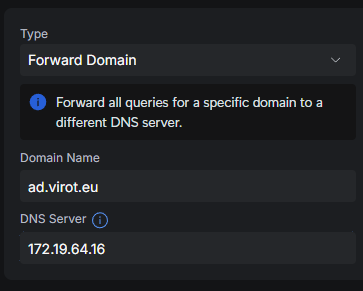
Others firewall vendors
I know most other firewall vendors allows this too