For one of my customers I was looking up the correct way of activating BitLocker while using Specops Deploy / OS. So after a little searching on google I understood that I will be in uncharted territory. Well after looking around how my customer currently implemented BitLocker I was able to solve it. This solution is not dependent on any manual changes to the MDT, so its a clean Deploy / OS solution.
Changes to installation group policy
So lets open up our installation GPO, and go straight down to the Specops Deploy / OS parts. Now edit the installation policy and go to the Custom MDT Properties and add the following variables:
| Variable Name | Value | Description |
|---|---|---|
| DoNotCreateExtraPartition | NO | Allows the installer to create required partitions on the drive. |
| BdeInstallSuppress | NO | Setting this to anything but YES will start the BDE installation |
After doing that all required changes to the installation policy is done.
Save the numerical recovery password to the Active Directory.
Most customers want to be able to access the drive if/when the computer/TPM chip dies. So we need to store the numerical recovery password in another location. So the regular choices are:
Manual, risking to forget and getting into trouble. Store in share, better but still more complex than required Store in AD, safe secure and redundant.
So how do we make sure the clients store the recovery password in the AD. Well first of are you running an active directory schema of 2008 or later you are practically done. Otherwise you could extend the Schema to include the Bitlocker parts, or as I would suggest extend the schema with Windows 2012R2. See link below for more information if you dont want to extend schema to Windows 2008 or later. Windows will store the recovery password in an object called ms-FVE-RecoveryInformation that is located below the computer object. This helps in cleanup as when the computer is deleted so is all the keys.
So now we have extended the schema. We still need to instruct our workstations to save the password to the AD. Well here I would suggest going the Group Policy route mostly because I really likes GPOs.
So lets fire up our Group Policy Management Console (gpmc.msc). Create a new GPO for the Bitlocker settings or select another GPO. Edit the selected GPO
You are now facing two different places to edit depending on if you are deploying Vista or later.
Window Vista
- Location: Computer Configuration\Policies\Administrative Templates\Windows Components\Bitlocker Drive Encryption
- Setting: Store BitLocker recovery information in Active Directory Domain Services
- Value: Enabled
Window 7 or later
- Location: Computer Configuration\Policies\Administrative Templates\Windows Components\Bitlocker Drive Encryption\Operating System Drives
- Setting: Choose how BitLocker-protected operating system drives can be recovered
- Value: Enabled
Don’t forget to check the box that says Do not enable BitLocker until recovery information is stored to AD DS for operating system drives.
Start the installation
So after being bored for a while looking at a screen doing nothing, the install is complete. We login to the client and open a cmd windows as administrator so we can check the progress. And what do you know, it is encrypting the drive as I am writing this.
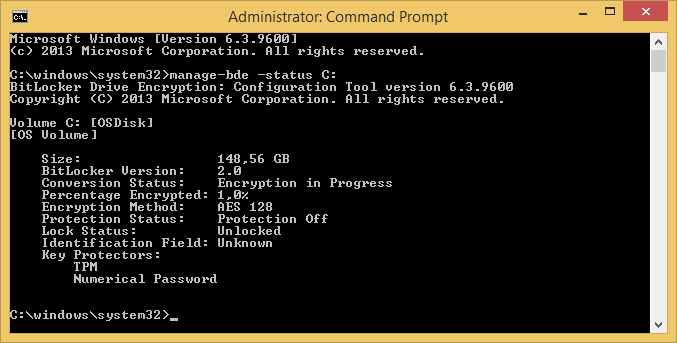
Sources: