So In my last blog I talked about the possibility of faking a password change, by setting the last time the password was changed.
So lets find out if somebody has been tampered with.
To do this we check the last time somebody updated the pwdlastset attribute and compare to the last time somebody updated the ntPwdHistory attribute.
If you change passwords the AD will update both. Also I added an allowance for 10 if you needed to check or uncheck the password must be changed checkbox.
The AD does store loads of data that most people never see or have to see, One such attribute is the last time an attribute was updated.
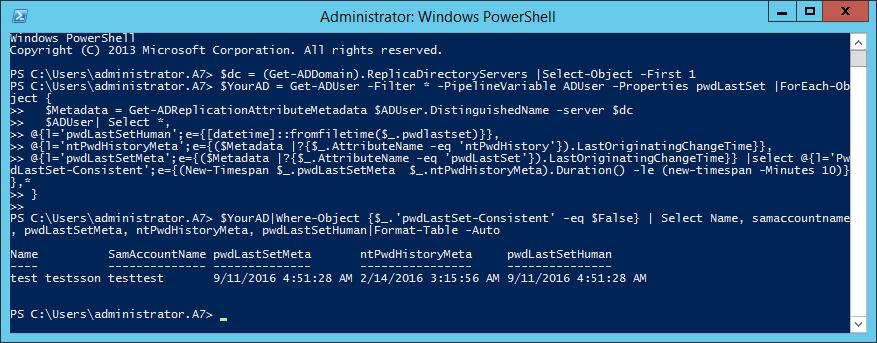
The script
$dc = (Get-ADDomain).ReplicaDirectoryServers |Select-Object -First 1
$YourAD = Get-ADUser -Filter * -PipelineVariable ADUser -Properties pwdLastSet |ForEach-Object {
$Metadata = Get-ADReplicationAttributeMetadata $ADUser.DistinguishedName -server $dc -Properties pwdlastSet,ntPwdHistory
$ADUser| Select *,
@{l='pwdLastSetHuman';e={[datetime]::fromfiletime($_.pwdlastset)}},
@{l='ntPwdHistoryMeta';e={($Metadata |?{$_.AttributeName -eq 'ntPwdHistory'}).LastOriginatingChangeTime}},
@{l='pwdLastSetMeta';e={($Metadata |?{$_.AttributeName -eq 'pwdLastSet'}).LastOriginatingChangeTime}} |select @{l='PwdLastSet-Consistent';e={(New-Timespan $_.pwdLastSetMeta $_.ntPwdHistoryMeta).Duration() -le (new-timespan -Minutes 10)}},*
}
$YourAD|Where-Object {$_.'pwdLastSet-Consistent' -eq $False} | Select Name, samaccountname, pwdLastSetMeta, ntPwdHistoryMeta, pwdLastSetHuman|Format-Table -Auto