So I needed to do gather some information on the usage on a Fileserver so we enabled auditing but those logs aren’t that fun.
Using the event viewer isn’t really an option with thousands of logentries to process.
So I went to Powershell which has Get-WinEvent which returns [System.Diagnostics.Eventing.Reader.EventRecord] objects.
But those still isnt that fun, they are event logs so I cant just do a Where-Object search on them as the message is a textblock.
BUT I can convert them into XML which allows me to do queries on the XML with Where-Object but that still is limiting as I needed to do convertions, and depending on Powershell version you can do it different ways.
So I did a cmdlet to do those for me so I dont have to in the future.
It reads the events you throw at it and create a translation map from the XML to a Powershell object.
So I created ConvertFrom-VirotEvent, a small sample below.
Lets see all times somebody used runas, eleveted them selfs using UAC or RDP.. Well anytime windows presented a loginbox for an already logged on user. Or other process did this to as the taskscheduler.
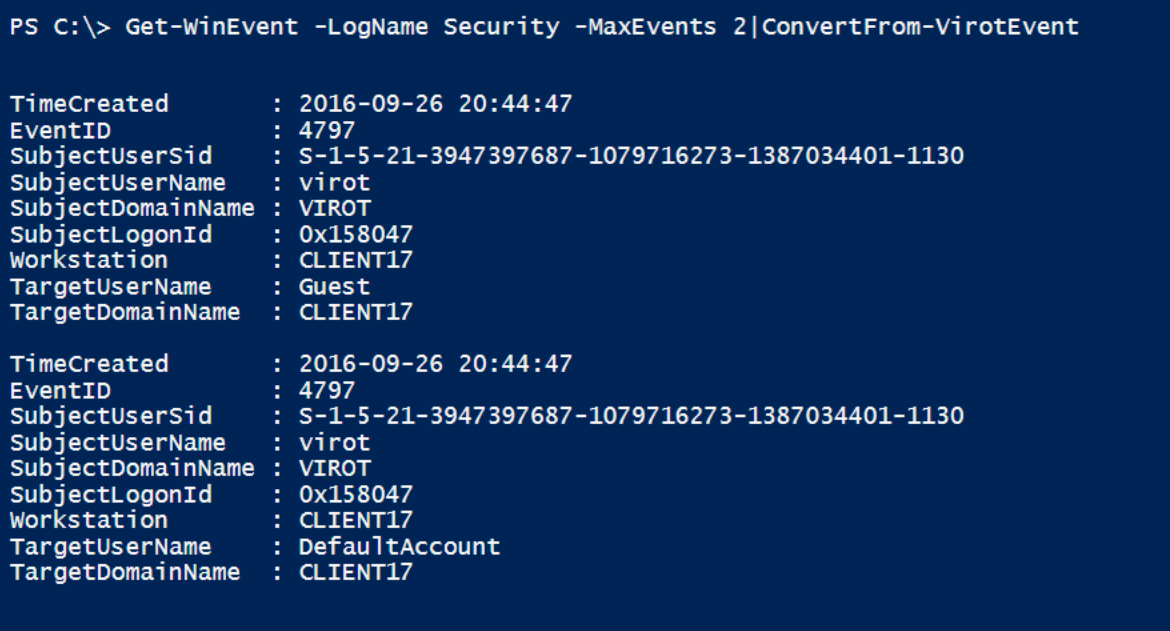
$Events = Get-WinEvent -FilterHashtable @{'LogName'='Security';'Id'='4648'}
$Events2 = $Events | ConvertFrom-VirotEvent
$Events2 |select TimeCreated, SubjectUserName, SubjectDomainName, TargetInfo$Events = Get-WinEvent -FilterHashtable @{'LogName'='Security';'Id'='4648'}
$Events2 = $Events | ConvertFrom-VirotEvent
$Events2 |Group SubjectUSerName|Select Name, Count |Sort Count -Descending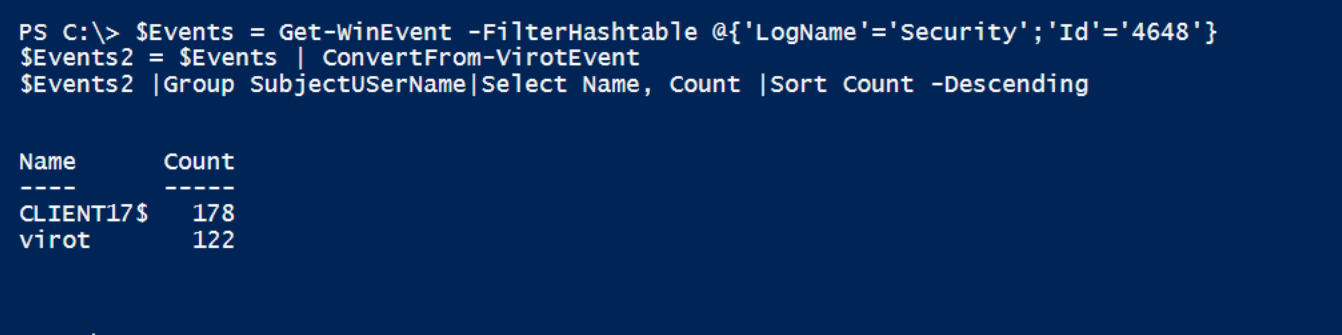
Download
You can download the script from the Microsoft Technet Galleries.
Since Microsoft closed Technet Galleries I have made the script available on github, I have also renamed it to follow naming more. It’s now ConvertTo-VirotEventObject.