Cheapish
So spending $129 isn’t cheap, but compared to everyone else it is cheaper. So why would I spend $129?
Well i have been developing my
Powershell Yubikey module
. And when I started going into the formating, well that is something that Microsoft seems to be a tad protective about. So I when the module is on the network I got this kind of faults:
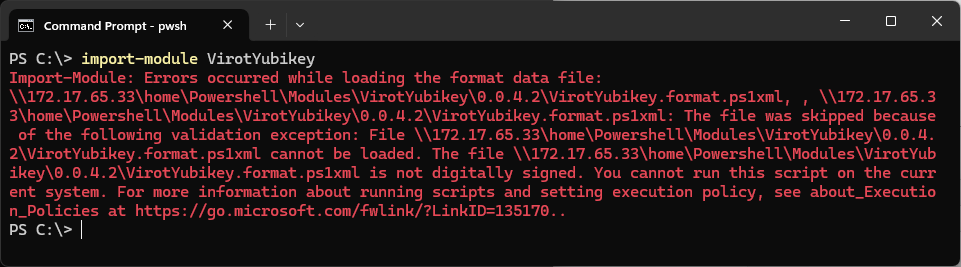
Why even sign?
I want my software to work. I want to reduce the amount of warnings. Then the way forward is to sign your stuff.
Did I cheap out?
I don’t think the reason I am getting a untrusted publisher warning, is that I opted for the OV instead of EV. Microsoft gets those warnings. So I just think it is if you dont explicitly trusts the publisher you will get this kind of warning.
SSL.COM
So I opted for the cheapest provider I could find. I went with SSL.COM. So why am I writing this, well remember the powershell module . We can use that one together with their instructions to simplify things. SSL.COM does have their own instructions on how to do this, but I feel that the powershell module is easier than the Yubikey Manager commands they are recommending.
So what do we need:
- A FIPS Series Yubikey, Must be FIPS
- My powershell module
- $129 to spend for a Code Signing Certificate at ssl.com
What to do
The following is based on that the Yubikey is bland and has zero configuration done before.
- Install the powershell module
Install-Module powershellYK - Set up the PIN / PUK codes
You can easily get a secureString by running: (Read-Host -AsSecureString -Prompt ‘PIN’)
Set-YubikeyPIV -PIN (Read-Host -AsSecureString -Prompt 'Current PIN') -NewPIN (Read-Host -AsSecureString -Prompt 'New PIN') Set-YubikeyPIV -PUK (Read-Host -AsSecureString -Prompt 'Current PUK') -NewPUK (Read-Host -AsSecureString -Prompt 'New PUK') - Create a new key needs to be minimum EccP384, RSA3072 or RSA4096 (RSA3072 and above only available in Yubikey version 5.7)
New-YubikeyPIVKey -Slot 0x9a -Algorithm EccP384 New-YubikeyPIVKey -Slot 0x9a -Algorithm RSA3072 New-YubikeyPIVKey -Slot 0x9a -Algorithm RSA4096 - Generate the attestion certificate for the slot
Assert-YubikeyPIV -Slot 0x9a -PEMEncoded - Generate the intermediate certificate for the Yubikey
Export-YubikeyPIVCertificate -AttestationIntermediateCertificate -PEMEncoded - Buy a Code Signing Certificate from ssl.com
- Continue using Step3 in the official documentation
- Wait until the organizational checks are done
- Download the Yubikey Installation (DER)
- Install the certificate into Yubikey
Import-YubikeyPIVCertificate -Slot 0x9a -Path \temp\SignedCertificate.cer - Make sure to have the Minidriver installed
- Start signing stuff
So I was really stumped, where do I enter the CSR? Well, they are smart. They are using the fact that the attestation certificate has the same public key. So they dont need the CSR they have all the info and it works.