Lets show the recipient of your Certificate Request we mean business
Certificates Requests (CSR) can contain more than just the request. I am using my powershell module . Sure yubico-piv-tool has the same functionallity. But if you are running in Windows, Powershell is the scripting language to support.
So lets create a new Certificate Request and include the Attestion and Intermediate certificates to allow for immediate verification. We can see that the CSR is same as the attestion certificate created on the Yubikey, that we have a real chain back to Yubico.
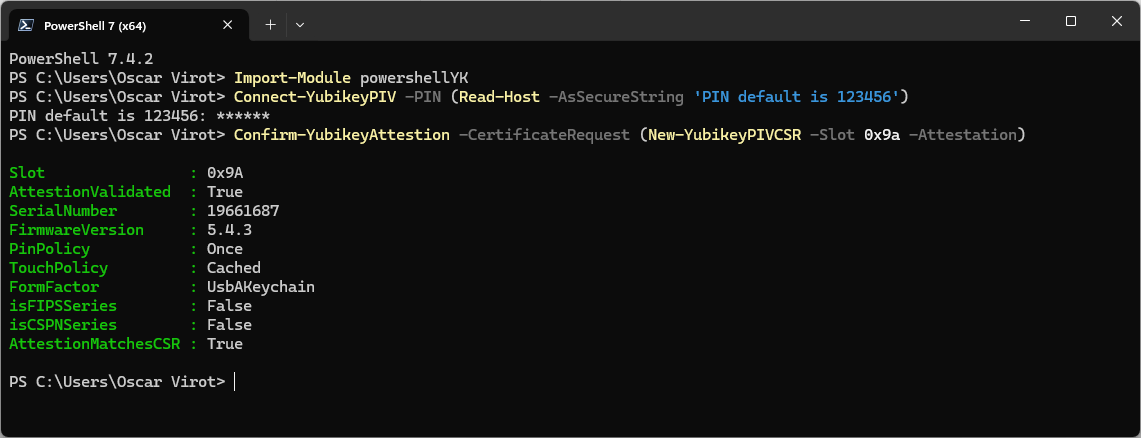
This will work out of the box on a new Yubikey, because that has never changed any settings. If you just want to try, remember to connect to the Yubikey PIV part with the correct PIN.
Import-Module powershellYK
Connect-YubikeyPIV -PIN (Read-Host -AsSecureString 'PIN default is 123456')
Confirm-YubikeyAttestion -CertificateRequest (New-YubikeyPIVCSR -Slot 0x9a -Attestation)We can ofcource also just verify the attestion and intermediate certificates
We can verify the attestion and intermediate certificates too. The attestion certificate uses the same key as the slot you are working with,
ssl.com
uses just the attestion and intermediate to issue your code signing certificate.
This allows us to verify that the CSR is for the same key as the attestioncertificate, then we have the intermediate certificate which is signed by Yubico at manufacturing and is used to sign the attestion certificate.
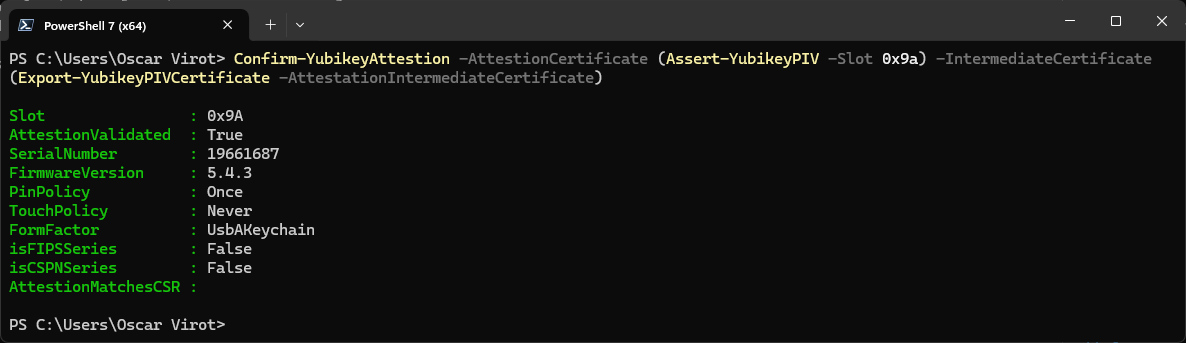
Confirm-YubikeyAttestion -AttestionCertificate (Assert-YubikeyPIV -Slot 0x9a) -IntermediateCertificate (Export-YubikeyPIVCertificate -AttestationIntermediateCertificate)Ofcource we can just check two files too. No need to have a Yubikey at all, the Confirm-YubikeyAttestion supports PEM files, PEM strings in addition to X509Certificate2 object.
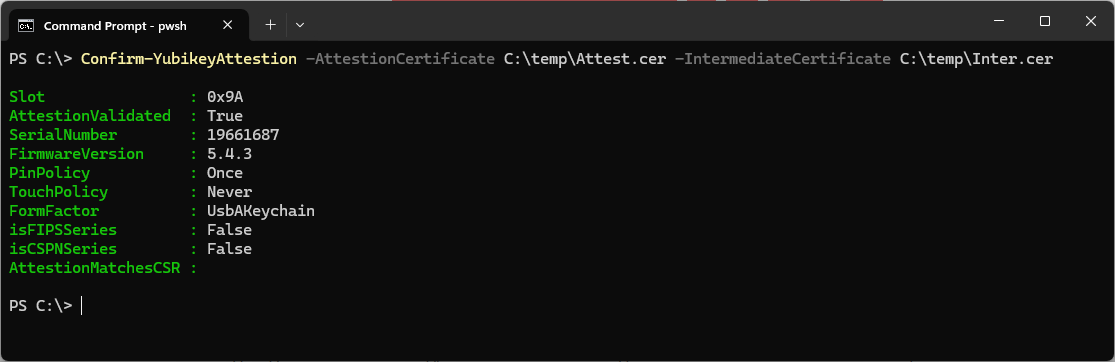
Confirm-YubikeyAttestion -AttestionCertificate C:\temp\Attest.cer -IntermediateCertificate C:\temp\Inter.cer